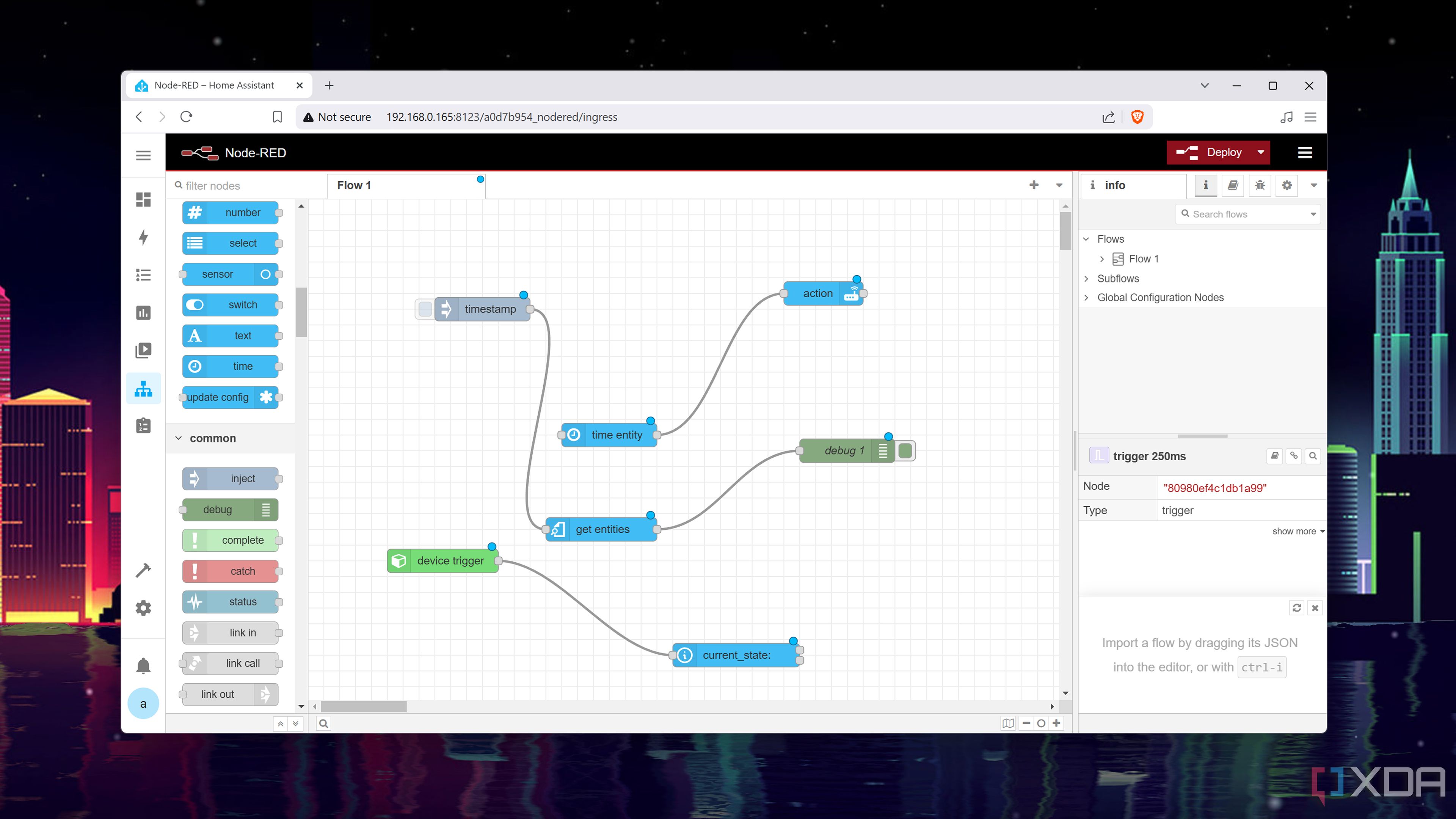
Too many software supply chain defense bibles? Boffins distill advice
How to avoid another SolarWinds, Log4j, and XZ Utils situation Organizations concerned about software supply chain attacks should focus on role-based access control, system monitoring, and boundary protection, according to a new preprint paper on the topic.…

How to avoid another SolarWinds, Log4j, and XZ Utils situation
Organizations concerned about software supply chain attacks should focus on role-based access control, system monitoring, and boundary protection, according to a new preprint paper on the topic.…


















![Mobile Legends: Bang Bang [MLBB] Free Redeem Codes March 2025](https://www.talkandroid.com/wp-content/uploads/2024/07/Screenshot_20240704-093036_Mobile-Legends-Bang-Bang.jpg)